Reverse engineering is a powerful technique used to understand how Android applications work by analyzing the code that constitutes the application. In this guide, we’ll explore how to reverse engineer Android APK files using Jadx-GUI, a popular tool for decompiling Android apps. We’ll also go through the installation process on Windows, macOS, and Linux, and explain how to find APK files to practice on.
What Is Reverse Engineering?
Reverse engineering refers to the process of taking apart a software program or application to understand its internal workings. In the case of Android applications, this usually involves decompiling the APK (Android Package) file to extract and analyze the source code. This process can be useful for:
- Finding vulnerabilities in apps.
- Learning how a certain feature is implemented.
- Recovering lost code.
- Ensuring security compliance.
However, reverse engineering may also have ethical and legal implications. Always ensure that you have the permission of the app developer before decompiling and analyzing an application.
Getting APK Files
Before we begin the reverse engineering process, we need an APK file to work on. APK files are packaged binaries of Android apps that can be downloaded from various sources such as APKPure, which offers a wide variety of APKs from different applications.
Step 1: Visit APKPure to download APK files for the application you want to reverse engineer.
Step 2: Ensure that you’re downloading the correct APK version that you are interested in reverse engineering.
Introduction to Jadx-GUI
Jadx-GUI is an open-source tool used to decompile Android APKs into readable Java code. It is especially popular among security researchers and developers looking to understand the internal logic of an app.
Jadx-GUI works by converting the DEX (Dalvik Executable) bytecode inside an APK file into Java source code, which can then be read and analyzed. This tool is available on Windows, macOS, and Linux.
How to Install Jadx-GUI on Windows, macOS, and Linux
You can install Jadx-GUI on all major operating systems by following these steps:
Installing Jadx-GUI on Windows
Step 1: Go to the Jadx GitHub releases page and download the latest Jadx release for Windows (typically available as a .zip file).
Step 2: Unzip the downloaded file to your desired location.
Step 3: Navigate to the unzipped folder and double-click on the jadx-gui.bat file to run the GUI version of Jadx.
Installing Jadx-GUI on macOS
Step 1: Install Homebrew if you haven’t already. Open Terminal and run:
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh)"Step 2: Once Homebrew is installed, run the following command to install Jadx:
brew install jadxStep 3: Launch Jadx GUI by typing:
jadx-gui
Installing Jadx-GUI on Linux
Step 1: Open a terminal and run the following commands to install Jadx:
sudo apt update
sudo apt install jadxStep 2: To run the Jadx-GUI, type:
jadx-guiHow to Use Jadx-GUI for APK Decompiling
Now that Jadx-GUI is installed, let’s go over how to decompile an APK.
Step 1: Launch Jadx-GUI from your system.
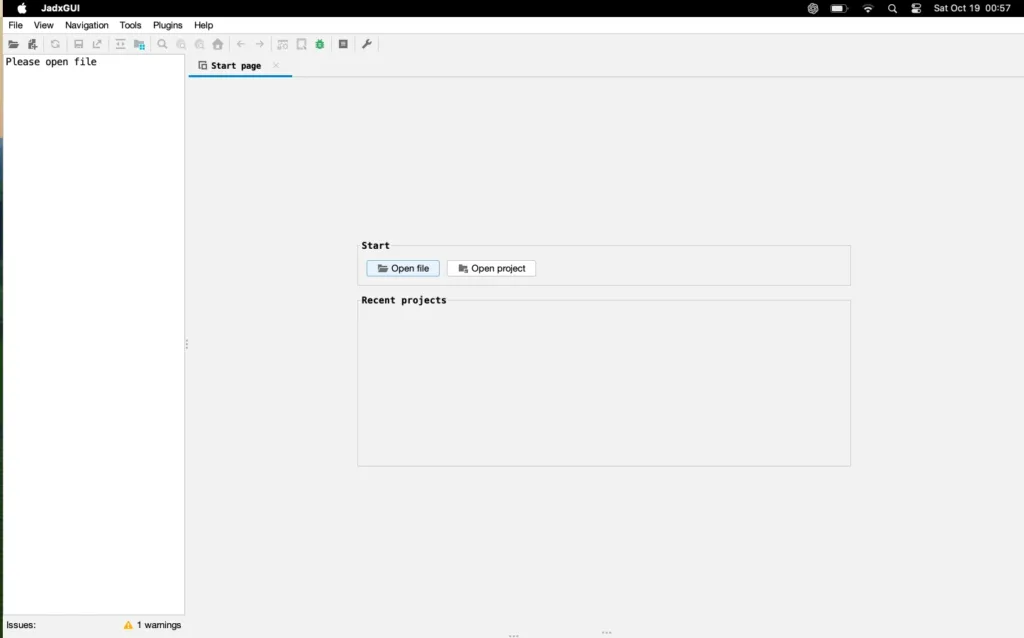
Step 2: Open the APK file you downloaded (apkpure.com) earlier by clicking “File” > “Open File”. Select the APK you want to reverse engineer.

Navigating the Jadx-GUI Interface
When you open an APK file in Jadx-GUI, you will see the application’s file structure on the left panel. Jadx-GUI provides an easy-to-navigate folder structure where you can see decompiled Java classes, resources, and manifest files. The top menu also provides additional options such as search and decompile settings.
- Java classes: Here, you will find the actual decompiled source code. You can click on each file to view the code in the right panel.
- Resources: This includes files like layout XML, assets, and string resources.
- Manifest: The AndroidManifest.xml file, which holds important app configuration details, is located here.
Reading Decompiled Code
Once you select a Java class, Jadx-GUI will display the decompiled Java code in the main panel. From here, you can inspect methods, variables, and API calls used by the app. For example, you might want to examine how network requests are handled or how certain permissions are requested in the code.
Here’s a simple example of decompiled code from C69225VvP.class for instagram apk;

This compiled Java code shows some of the APIs used by the Instagram application.
How to find what you are looking for?
You can search on jadx-gui using the control + shift + F5 key combination.
If you are looking for an http request, for example, you can find what you want by searching for words like “http”, “/api”, “@GET”.
To understand how a view is made, open the application on your device and search for the texts you see, you will definitely find the code lines you want by catching them somewhere.
These codes may seem difficult to read, but this will not give you the source codes as they are, it will give you ideas on how to make your developments better, this will be useful for you.
Remember, jadx-gui is not a bread to be eaten, it is just dough. In other words, take the ideas and then apply them to your code.
Gorkem KARA
Modifying Decompiled Code
While Jadx-GUI allows you to decompile and inspect code, it does not directly support recompiling APKs. If you wish to modify the decompiled code and recompile the APK, additional tools like ApkTool or Android Studio are required.
Useful Resources
For more information about Android reverse engineering and security practices, check out these resources:
- APKPure – Download APKs
- Jadx GitHub Repository
- Android Security Best Practices
- Understanding Mobile App Architecture
Reverse engineering Android apps using Jadx-GUI is an effective way to analyze how apps work under the hood. Whether you’re looking to learn from existing code, find vulnerabilities, or recover lost source code, Jadx-GUI offers an intuitive way to decompile APKs into readable Java source code. Just remember to always obtain permission when working with third-party applications!
For additional tips on improving your Android development skills, take a look at some of our other guides, like Concurrency in Kotlin Using Coroutines and Advanced Navigation Techniques in Jetpack Compose.
Did you like this article?
You can subscribe to my newsletter below and get updates about my new articles.